Compliance Monitoring: #
1. Using Argus for PCI DSS Compliance #
Overview #
The purpose of the Payment Card Industry Data Security Standard (PCI DSS) is to guarantee the safety of credit card data. Argus’s many features can assist in achieving a number of PCI DSS criteria.
Argus Capabilities for PCI DSS #
- Log Data Analysis
- Configuration Assessment
- Malware Detection
- File Integrity Monitoring (FIM)
- Vulnerability Detection
- Active Response
- System Inventory
- Visualization and Dashboard
Configuration Steps #
- Log Data Analysis:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > PCI DSS.
- Configuration:
- It enables log collection from sources such as web servers and databases.
- It sets up correlation rules to detect suspicious activities.
- Usage:
- It monitors log data for unusual patterns.
- It investigates and responds to detected anomalies.
- Configuration Assessment:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > PCI DSS.
- Configuration:
- It sets assessment criteria based on PCI DSS requirements.
- Usage:
- It regularly reviews system configurations for compliance.
- It adjusts configurations to address non-compliance issues.
- Malware Detection:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > PCI DSS.
- Configuration:
- It enables scanning for malware on critical systems.
- Usage:
- It monitors alerts for detected malware.
- It takes immediate action to isolate and remove malware.
- File Integrity Monitoring (FIM):
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > PCI DSS.
- Configuration:
- It adds directories and files to monitor.
- It configures alert thresholds for unauthorized changes.
- Usage:
- It regularly reviews FIM alerts for unauthorized changes.
- It investigates and remediates any suspicious changes to ensure file integrity.
- Vulnerability Detection:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > PCI DSS.
- Configuration:
- It schedules regular scans of your systems and applications.
- Usage:
- It reviews scan results to identify vulnerabilities.
- It applies patches and mitigations to address vulnerabilities promptly.
- Active Response:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > PCI DSS.
- Configuration:
- It sets up automated responses to certain security events.
- Usage:
- It defines actions such as blocking IP addresses or disabling accounts.
- It monitors and adjusts response actions as needed.
- System Inventory:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > PCI DSS.
- Configuration:
- It lists all of the software and hardware resources.
- Usage:
- It regularly updates and reviews the inventory.
- It ensures all assets are accounted for and secure.
- Visualization and Dashboard:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > PCI DSS.
- Configuration:
- It Customizes the dashboard to display relevant compliance metrics.
- Usage:
- It monitors the dashboard for real-time insights into your compliance status.
- It uses visualizations to quickly identify and address security issues.
2. Using Argus for GDPR Compliance #
Overview #
Within the EU, individual privacy and data protection are the main concerns of the General Data Protection Regulation (GDPR).
Argus Capabilities for GDPR #
- GDPR II, Principles
- GDPR III, Rights of the Data Subject
- GDPR IV, Controller and Processor
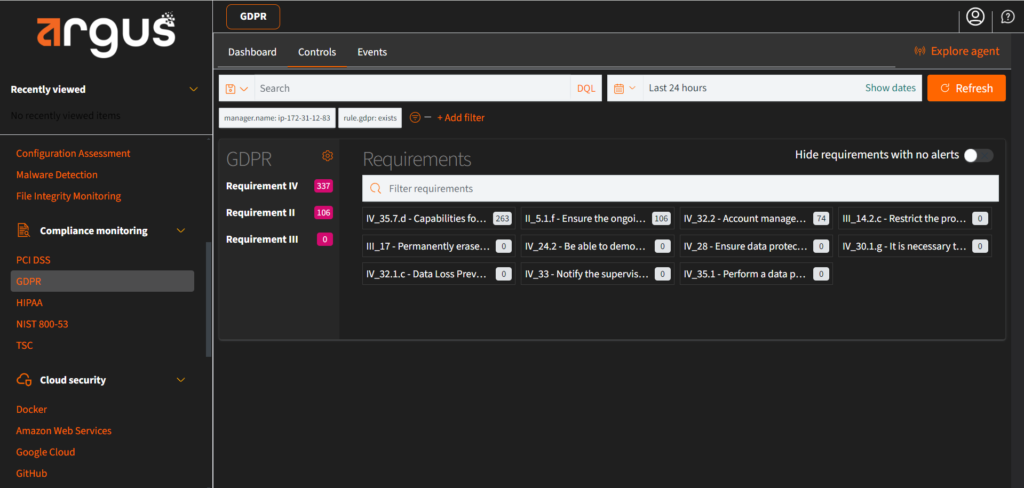
Configuration Steps #
- GDPR II, Principles:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > GDPR.
- Configuration:
- It defines and enforces data protection principles.
- Usage:
- It regularly reviews and ensures compliance with GDPR principles.
- It documents and addresses any deviations.
- GDPR III, Rights of the Data Subject:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > GDPR.
- Configuration:
- It implements mechanisms to handle data subject requests.
- Usage:
- It ensures timely response to data access, rectification, and erasure requests.
- It documents compliance with data subject rights.
- GDPR IV, Controller and Processor:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > GDPR.
- Configuration:
- It defines roles and responsibilities for data controllers and processors.
- Usage:
- It Regularly reviews and updates data processing agreements.
- It ensures compliance with controller and processor obligations.
3. Using Argus for HIPAA Compliance #
Overview #
HIPAA provides guidelines for safeguarding private client information.
Argus Capabilities for HIPAA #
- Visualization and Dashboard
- Log Data Analysis
- Configuration Assessment
- Malware Detection
- File Integrity Monitoring (FIM)
- Vulnerability Detection
- Active Response
Configuration Steps #
- Visualization and Dashboard:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > HIPAA > Dashboard.
- Configuration:
- It customizes the dashboard to display HIPAA-related metrics.
- Usage:
- It monitors the dashboard for real-time insights into HIPAA compliance.
- It uses visualizations to quickly identify and address security issues.
- Log Data Analysis:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > HIPAA > Events.
- Configuration:
- It enables log collection from sources such as electronic health records (EHR) systems.
- It sets up correlation rules to detect suspicious activities.
- Usage:
- It monitors log data for unusual patterns.
- It investigates and responds to detected anomalies.
- Configuration Assessment:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > HIPAA.
- Configuration:
- It sets assessment criteria based on HIPAA requirements.
- Usage:
- It regularly reviews system configurations for compliance.
- It adjusts configurations to address non-compliance issues.
- Malware Detection:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > HIPAA
- Configuration:
- It enables scanning for malware on critical systems.
- Usage:
- It monitors alerts for detected malware.
- It takes immediate action to isolate and remove malware.
- File Integrity Monitoring (FIM):
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > HIPAA
- Configuration:
- It adds directories and files to monitor.
- It configures alert thresholds for unauthorized changes.
- Usage:
- It regularly reviews FIM alerts for unauthorized changes.
- It investigates and remediates any suspicious changes to ensure file integrity.
- Vulnerability Detection:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > HIPAA
- Configuration:
- It schedules regular scans of your systems and applications.
- Usage:
- It reviews scan results to identify vulnerabilities.
- It applies patches and mitigations to address vulnerabilities promptly.
- Active Response:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > HIPAA
- Configuration:
- It sets up automated responses to certain security events.
- Usage:
- It defines actions such as blocking IP addresses or disabling accounts.
- It monitors and adjusts response actions as needed.
4. Using Argus for NIST 800-53 Compliance #
Overview #
A list of security and privacy measures for government information systems and organizations may be found in NIST Special Publication 800-53.
Argus Capabilities for NIST 800-53 #
- Visualization and Dashboard
- Log Data Analysis
- Security Configuration Assessment
- Malware Detection
- File Integrity Monitoring (FIM)
- System Inventory
- Vulnerability Detection
- Active Response
- Threat Intelligence
Configuration Steps #
- Visualization and Dashboard:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53 > Dashboard.
- Configuration:
- It customizes the dashboard to display NIST 800-53-related metrics.
- Usage:
- It monitors the dashboard for real-time insights into compliance.
- It uses visualizations to quickly identify and address security issues.
- Log Data Analysis:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53 > Events.
- Configuration:
- It enables log collection from various sources.
- It sets up correlation rules to detect suspicious activities.
- Usage:
- It monitors log data for unusual patterns.
- It investigates and responds to detected anomalies.
- Security Configuration Assessment:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53.
- Configuration:
- It sets assessment criteria based on NIST 800-53 controls.
- Usage:
- It regularly reviews system configurations for compliance.
- It adjusts configurations to address non-compliance issues.
- Malware Detection:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53.
- Configuration:
- It enables scanning for malware on critical systems.
- Usage:
- It monitors alerts for detected malware.
- It takes immediate action to isolate and remove malware.
- File Integrity Monitoring (FIM):
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53.
- Configuration:
- It adds directories and files to monitor.
- It configures alert thresholds for unauthorized changes.
- Usage:
- It regularly reviews FIM alerts for unauthorized changes.
- It investigates and remediates any suspicious changes to ensure file integrity.
- System Inventory:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53.
- Configuration:
- It lists all hardware and software assets.
- Usage:
- It regularly updates and reviews the inventory.
- It ensures all assets are accounted for and secure.
- Vulnerability Detection:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53.
- Configuration:
- It schedules regular scans of your systems and applications.
- Usage:
- It reviews scan results to identify vulnerabilities.
- It applies patches and mitigations to address vulnerabilities promptly.
- Active Response:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53.
- Configuration:
- It sets up automated responses to certain security events.
- Usage:
- It defines actions such as blocking IP addresses or disabling accounts.
- It monitors and adjusts response actions as needed.
- Threat Intelligence:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > NIST 800-53.
- Configuration:
- It integrates threat intelligence feeds.
- Usage:
- It uses threat intelligence to inform security decisions.
- It adjusts security measures based on the latest threat data.
5. Using Argus for TSC Compliance #
Overview #
Security, availability, processing integrity, confidentiality, and privacy measures are all reviewed using the Trust Services Criteria (TSC).
Argus Capabilities for TSC #
- CC1: Control Environment
- CC2: Communication and Information
- CC3: Risk Management and Design and Implementation of Controls
- CC4: Control Activities
- CC5: Monitoring of Controls
- CC6: Logical and Physical Access Controls
- CC7: System Operations
- CC8: Change Management
- CC9: Risk Mitigation
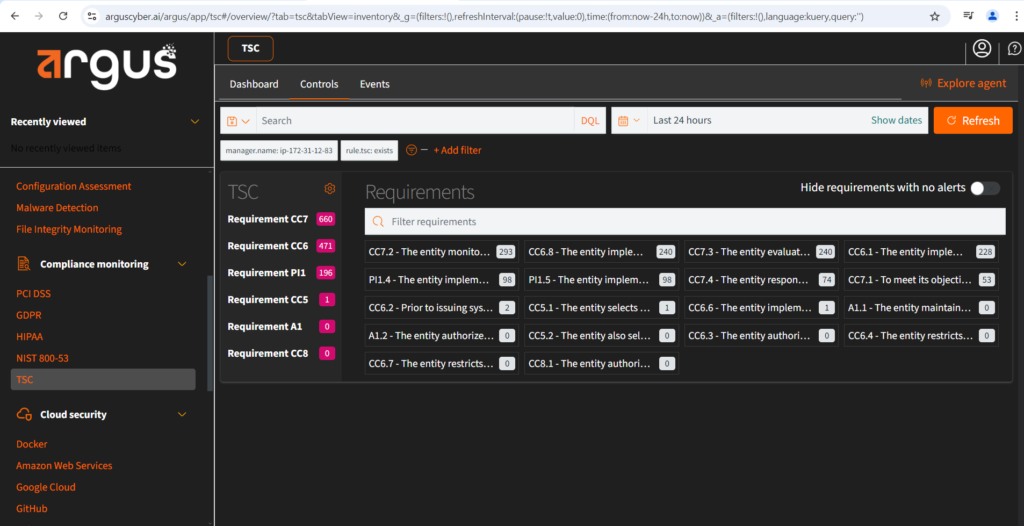
Configuration Steps #
- CC1: Control Environment:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It defines and documents your control environment.
- Usage:
- It regularly reviews and updates control documentation.
- It ensures the control environment meets TSC requirements.
- CC2: Communication and Information:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It implements mechanisms for effective communication.
- Usage:
- It regularly reviews communication channels.
- It ensures information is accurately conveyed.
- CC3: Risk Management and Design and Implementation of Controls:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It identifies and assess organizational risks.
- Usage:
- It documents and prioritizes risks.
- It implements controls to mitigate identified risks.
- CC4: Control Activities:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It defines control activities to address risks.
- Usage:
- It regularly reviews and updates control activities.
- Ensure controls are effective in mitigating risks.
- CC5: Monitoring of Controls:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It sets up monitoring for key controls.
- Usage:
- It regularly reviews monitoring data.
- It adjusts controls based on monitoring results.
- CC6: Logical and Physical Access Controls:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It implements access controls to protect sensitive data.
- Usage:
- It monitors and logs access to critical systems.
- It Regularly reviews and adjusts access permissions.
- CC7: System Operations:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It defines procedures for system operations.
- Usage:
- It regularly reviews and updates operational procedures.
- It ensures procedures meet TSC requirements.
- CC8: Change Management:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It implements change management processes.
- Usage:
- It regularly reviews and approves changes.
- It lists all changes to ensure traceability.
- CC9: Risk Mitigation:
- Where to Find in Argus: Navigate to Security > Compliance Monitoring > TSC.
- Configuration:
- It defines strategies to mitigate risks.
- Usage:
- It Regularly reviews and updates risk mitigation strategies.
- Ensure risks are effectively managed.




